Downloading and Installing Tor Browser
The only legitimate source for Tor Browser is the official Tor Project website. Third-party download portals, file-sharing platforms, and app stores frequently distribute tampered versions containing surveillance payloads or cryptocurrency-stealing malware. After downloading the installer for your operating system, verify the cryptographic signature using the Tor Project's signing key before proceeding with installation. On Windows, run the installer and choose a directory that does not require administrative privileges. On Linux, extract the tarball and execute the start-tor-browser script from the extracted directory. macOS users should drag the application to the Applications folder after mounting the disk image.
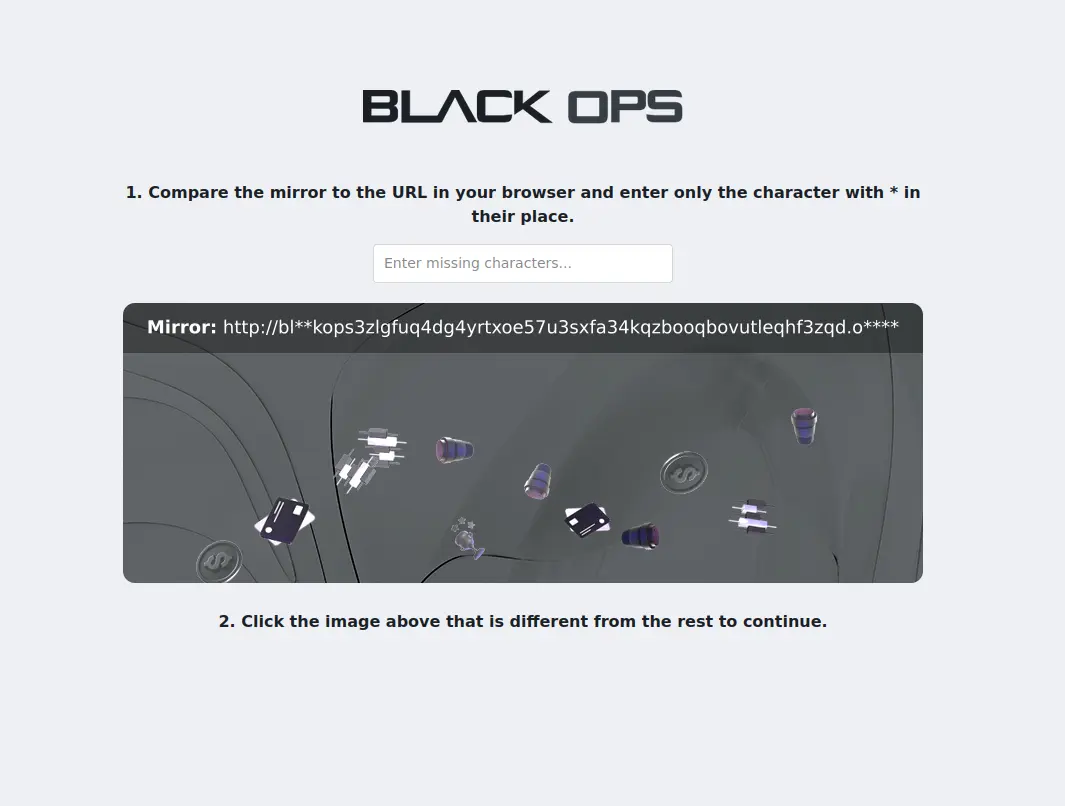
Configuring Browser Security to Safest Level
Immediately after launching Tor Browser for the first time, click the shield icon in the toolbar and set the security level to "Safest." This configuration disables JavaScript execution on all non-HTTPS sites, blocks certain font rendering mechanisms that can be exploited for fingerprinting, prevents media auto-play, and restricts several potentially dangerous browser features. BlackOps Market is engineered to function fully at this maximum security setting, so you sacrifice no marketplace functionality while gaining the strongest possible browser-level protection against exploitation attempts.
NoScript Configuration and Fingerprint Prevention
Tor Browser ships with the NoScript extension pre-installed. When the security level is set to Safest, NoScript blocks all JavaScript globally by default. Avoid adding per-site exceptions unless absolutely necessary, as each exception expands your attack surface and contributes to a unique browser fingerprint. Never resize the Tor Browser window from its default dimensions, as window size is one of the most reliable fingerprinting vectors. Refrain from installing additional extensions, changing default fonts, or modifying any about:config preferences — each modification makes your browser instance distinguishable from the millions of standard Tor Browser installations in the network.
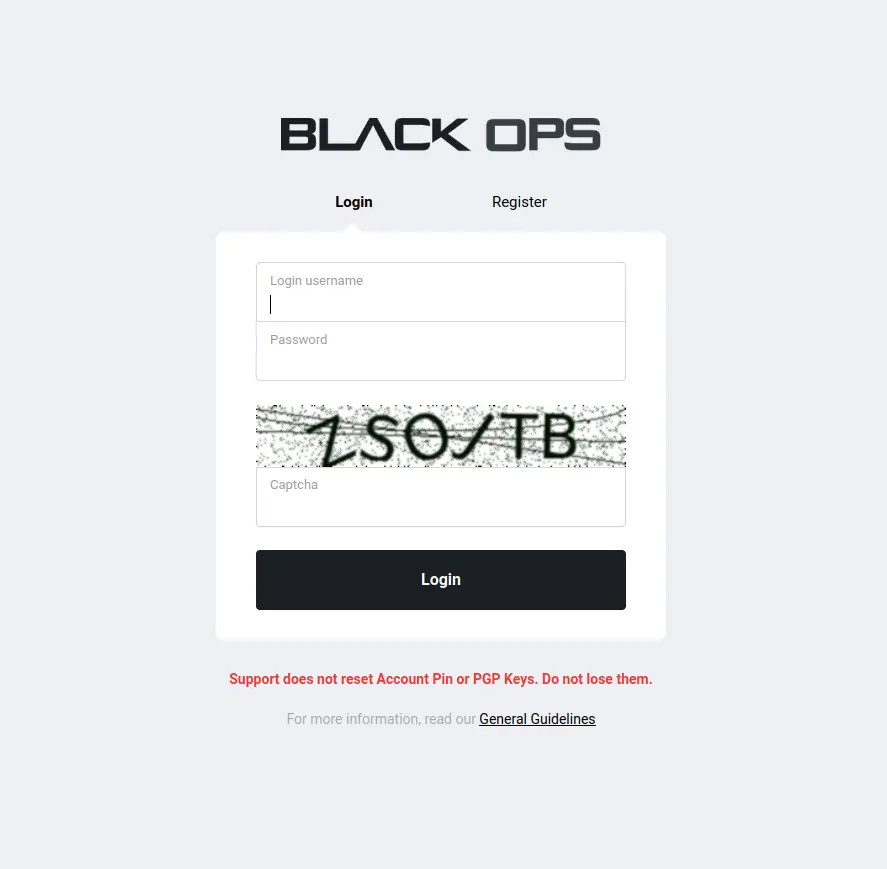
First-Time Connection Procedure
With Tor Browser configured, copy one of the verified onion addresses from the mirror section above. Paste it directly into the address bar and press Enter. The initial connection establishment typically requires 10 to 30 seconds as Tor constructs a six-hop circuit through the relay network to reach the hidden service. When the login page loads, inspect the address bar carefully to confirm it matches the address you entered character by character. Look for BlackOps Market's anti-phishing verification challenge — a visual CAPTCHA unique to the genuine service. If anything appears unusual, such as missing interface elements, unexpected credential requests, or layout inconsistencies, close the tab immediately and attempt connection through an alternative mirror.
Post-Connection Security Checklist
After successfully reaching BlackOps Market, bookmark the verified address in Tor Browser for future sessions. Enable PGP-based two-factor authentication through the account security settings to protect against credential theft. Generate a dedicated 4096-bit RSA key pair using GnuPG exclusively for your marketplace identity. Upload your public key to your profile and test the decryption challenge to confirm proper configuration. Store your marketplace credentials in KeePassXC using a strong master passphrase rather than relying on memory or unencrypted notes.
Recommended Operating Systems for Secure Access
For maximum operational security when accessing BlackOps Market, consider using a dedicated privacy-focused operating system rather than your everyday desktop environment. Tails OS is an amnesic live system that boots from USB media, routes all network traffic through Tor by default, and leaves absolutely no forensic traces on the host machine after shutdown. For users who prefer a persistent environment, Whonix provides a dual virtual machine architecture that isolates your browsing activity from your host operating system, making IP leaks architecturally impossible even if the workstation is compromised. Both systems represent significant security improvements over running Tor Browser on a standard Windows or macOS installation, where background processes, automatic updates, and system telemetry can inadvertently compromise your anonymity. Encrypt your boot media using VeraCrypt volumes to protect any persistent storage from physical examination. Review the Electronic Frontier Foundation guidelines on digital self-defense and consult Privacy Guides for current recommendations on privacy-respecting software configurations. Managing your cryptographic keys with OpenPGP compliant tools ensures interoperability across all platforms that support PGP-based authentication.